There are lessons to be learned from celeb iPhone pic thefts – but they’re not what you might have heard
It’s time to stop victim-blaming, and time to start yelling at tech companies - and everyone else - about better online security

It was all I could do to stop myself hurling expensive kit out of the window on reading about the recent ‘celeb nude photo scandal’.
Knee-jerk reactions typically consisted of “serves them right” as though punishment was warranted for being famous, a woman, and sharing the odd nude photo with a partner.
Then there was the sage advice that people “shouldn’t take nude photos” if they don’t want them ‘leaked’ and shared with the world. But this wasn’t so much a scandal as a brazen, despicable breach of people’s privacy. And the photos weren’t leaked – they were stolen by hackers and fired across the internet, with no regard for the damage and pain such actions would cause.
If this was a scandal, it was only one in the sense tech companies too often take a ham-fisted, opaque approach to online security, hiding risk deep beneath layers of supposed convenience.
‘Click this and we’ll upload all your photos.’ No need to warn people about the potential consequences! No need to make people aware about what’s really happening! No need to tell people to secure online accounts with robust passwords, and to obfuscate answers to so-called security questions that can be prone to social engineering! So: no victim-blaming here.
What happened was awful for those involved, and it’s no more their fault than it would be yours if a burglar broke into your shed and stole your new bike. (“Ha! Shouldn’t own a new bike, fool!” might yell the aforementioned advice-givers, shortly before we at Stuff HQ hurl a furious swan at them.)
Instead: some tips. These won’t necessarily stop someone getting hold of your private data, but they’ll make doing so a whole lot harder.
READ MORE: An Apple games console would be a bad idea – and here’s why
1. Pa$$word is not a password
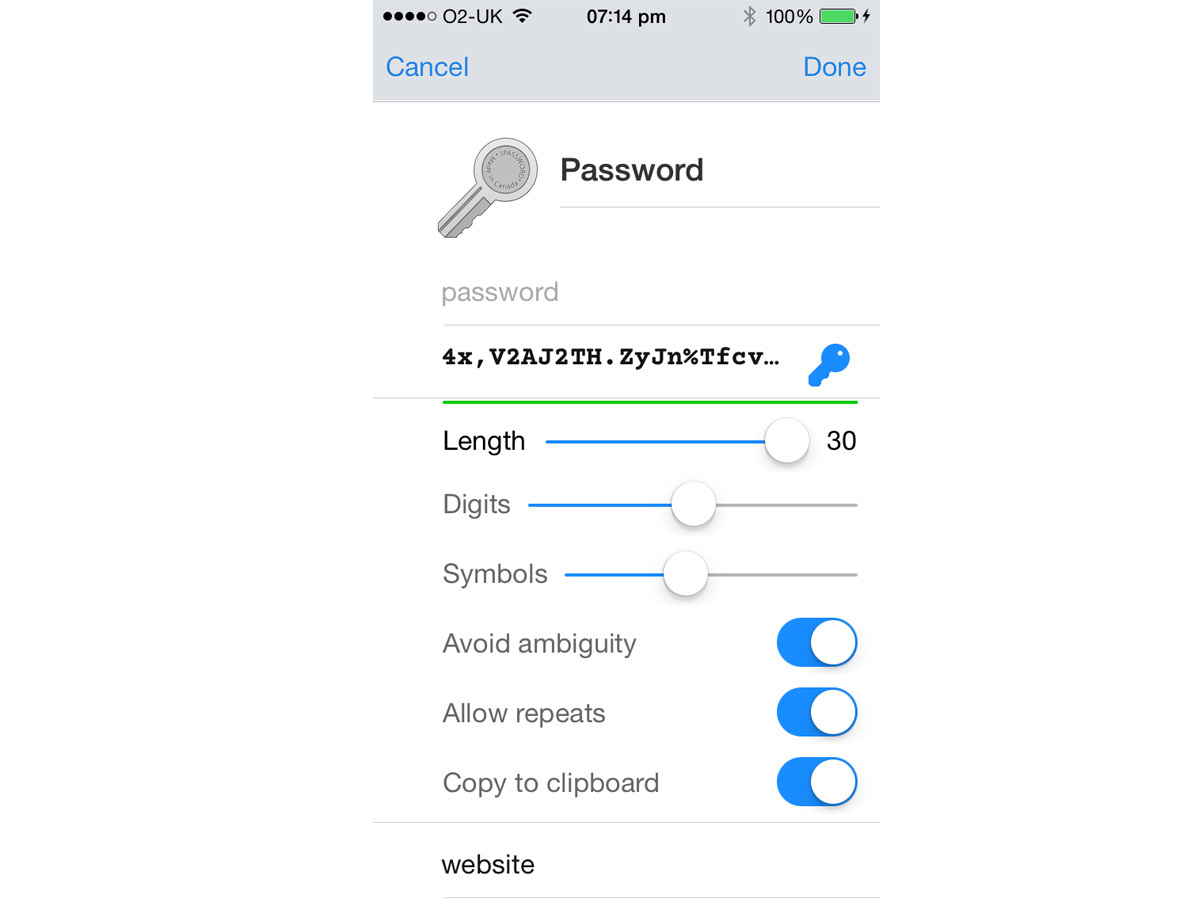
In a scene you’d swear was scripted by Chris Morris, CNN technology analyst Brett Larson suggests you make passwords more secure by changing ‘s’ characters to dollar signs. No. Passwords must be complex and not amenable to obvious guesswork.
Instead, use a password manager such as 1Password to create complex online passwords on your behalf and deal with logins so you don’t have to remember them.
2. Passwords should be unique
If all your passwords are the same (or use a pattern), you’re done for if someone breaks into one of your accounts.
Use a password manager to make complex, unique passwords for every online login.
3. Don’t be complacent about phishing
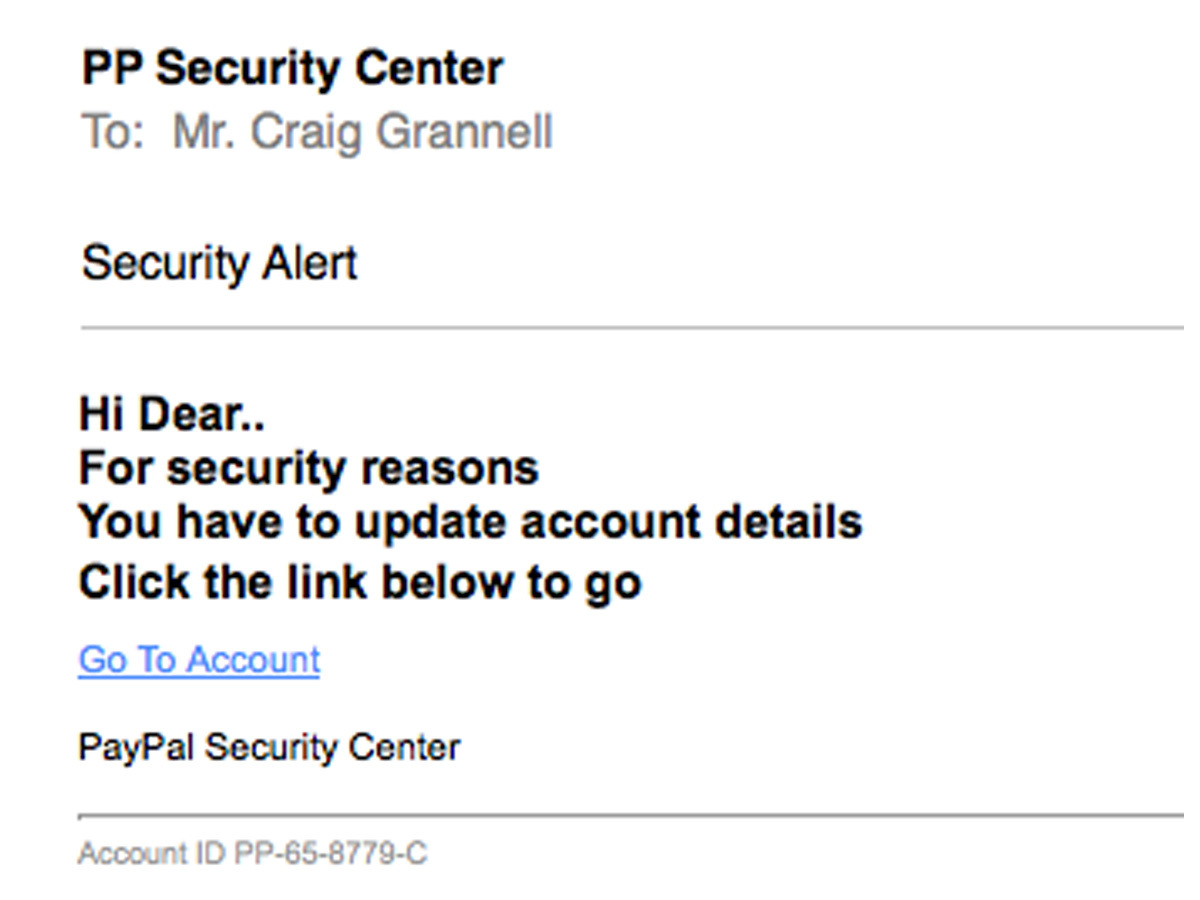
You might scoff at the idea of phishing when receiving an email from ‘Appple’ that in broken English says it ‘Need password reset your account compromize’.
But some phishing attempts are getting clever. Symantec noted a Google Docs scam hosted on Google’s own servers hoodwinked users, because it looked legit. Some outlets report the celebs whose photos were stolen could have been caught out in a similar manner.
So be wary of communications you weren’t expecting, doubly so if any demand you sign in somewhere. If sign-in is required, don’t click a link – login manually.
4. Use two-factor verification
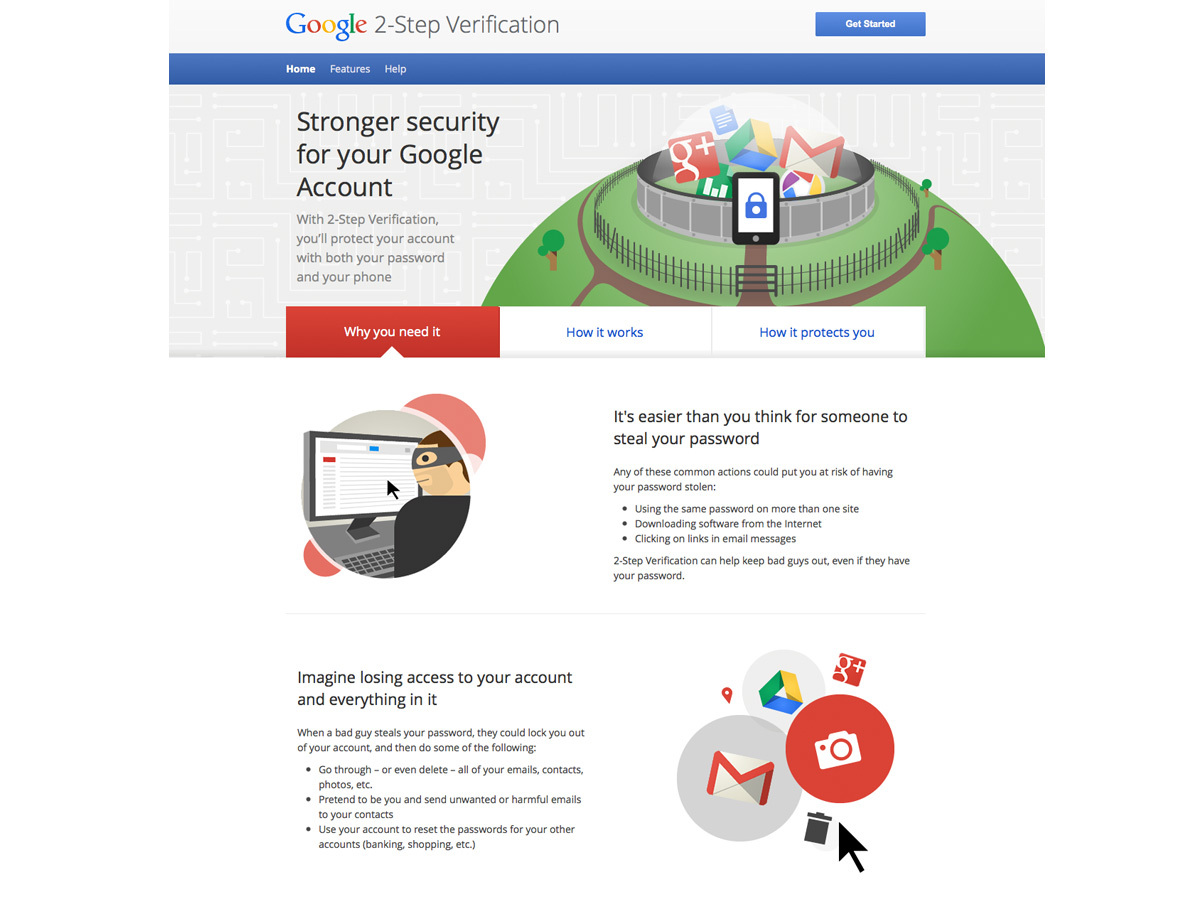
When you use two-factor verification, login only occurs when you have access to a secondary code on a trusted device, such as a smartphone. The code is used along with your password to access the account. Banks often provide two-factor verification, but so too do Google and Apple.
Note with Apple that a recovery key is provided and required should you forget your password and lose access to trusted devices. Do not lose the recovery key as well or you’ll be locked out of your account for good.
5. Secure your email
Plenty of hacks are achieved by guessing a username and sending a password reset to a compromised email account. Therefore, ensure your email is as secure as possible by utilising strong passwords and two-factor verification.
With Gmail, consider obfuscating logins to make them harder to guess by adding + and a random text string to your username (such as [email protected]) for services that support such addresses.
Again, the login can be stored in your password manager.
6. Obfuscate security answers
Plenty of online services – including Apple’s iCloud – demand you provide answers to security questions, which are then used as a line of defence for password resets and account access.
These can fall prey to social engineering (guessing details based on knowing facts about you) and brute-force attacks (repeatedly hitting the fields with relevant answers until the right ones are found).
Therefore, randomise them like you would a password and store the answers in your password manager.
7. Be aware of auto-uploads
Some cloud services upload photos taken with your smartphone. This may happen automatically, or you may have agreed to this during set-up. If you don’t want all your images in the cloud, it’s best to check what’s being sent there.
Dropbox’s Settings house a Camera Upload function; Flickr’s equivalent is called ‘Auto Sync’. iCloud is more complex, because your Camera Roll (local photo storage) can be backed up to iCloud, and Photo Stream (automatic photo-sync across devices) will separately store images for 30 days.
In iOS 8, this will reportedly change to all of your images and edits. If you don’t want any of your photos on Apple’s servers, take a trip to the Settings app. In iCloud > Storage & Backup > Manage Storage > [device], turn off Camera Roll and storage for any camera app you use, and also disable Photos > My Photo Stream.
Alternatively, if you take a single pic you later don’t want stored in the cloud, open Photos, select the Photos tab, tap Select, choose the image, then tap the trashcan.
8. Recognise this isn’t just an Apple thing
The press likes to slam Apple when problems occur with its services, but, as already noted, other cloud services aren’t free from security issues. So if you’re feeling smug with your Android smartphone, you might nonetheless want to check your app settings and passwords.
9. Encourage companies to do better
Finally, don’t be silent. If you’ve waded through Apple’s horrible two-step verification set-up, or found a Google app-specific password mysteriously no longer works, find the relevant feedback form and inform the companies where their processes are opaque and not terribly user-friendly.
Although dreadful PR causes companies to sit up and take notice, so too will a stream of complaints from users. If enough people demand better security that’s also easier to set-up, understand and use, that’s what we’ll all eventually get.
READ MORE: Stuff’s Apple iPhone 6 live blog and full preview