The Twelve X is Christopher Ward’s most sophisticated (and expensive) watch yet
The Twelve X features an open-hearted version of Christopher Ward’s Calibre SH21

LG 65QNED91T6A review: brighter means better
Mini-LED model plays catch-up to OLED in some areas, but impresses in others

This Elago MagSafe MS W5 stand gives your charger an irresistible retro gaming twist
1-up your desk setup by adding an Elago MagSafe MS W5 Charging Stand

Bulgari Octo Finissimo Ultra is so thin it practically disappears
And at €600,000 each, it’s a lot of money for not much watch

Latest posts
Best BBQ in the UK 2024: gas and charcoal barbeques
Sun’s out, buns out – the best BBQs to enhance your outdoor cooking experience

This is next season’s Formula E car, and it’s faster than an F1 car
The new Gen 3 Evo racing car will be used in Formula E’s 11th season next year, and it’s faster than F1 cars!

Best Ring doorbell 2024: which one is best for your home?
Find yourself the best Ring video doorbell for hassle-free home security, no matter your needs or budget. Ding dong!

Playseat Formula Intelligence F1 Edition is the perfect sim-racing cockpit for wannabe Lewis Hamiltons
If you can’t take pole position with the Playseat Formula Intelligence F1 Edition, it’s probably time to find a new hobby

Best upcoming Lego sets 2024: this year’s top new Lego releases
Prepare for a block party with these superb Lego sets, due out later this year

Features
Best soundbar 2024: TV sound for every budget reviewed
Upgrade your substandard TV speakers with superior sound and Dolby Atmos: we’ve tested the best soundbar for every home setup

Netflix password sharing crackdown: what to do about it if you share your Netflix login
The streaming giant is getting tough with freeloading friends and family

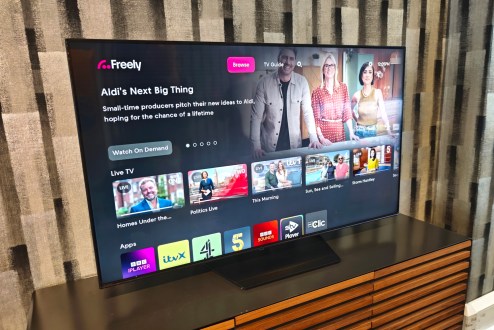
What is Freely? The BBC, ITV, C4 and C5 on demand service, explained
Updated: Hands-on with the new UK streaming service launching very soon
Microsoft Xbox One X vs Sony PlayStation 4 Pro: which is best?
Does the powerful new Xbox unseat Sony’s souped-up PS4?

Reviews
Fujifilm Instax Mini 99 review: all about the analogue approach
Light-based filters and exposure controls make this a treat for creative snappers

FiiO M23 review: one potent portable player
Put that smartphone down – a DAP this divine will get your portable audio properly sorted.

Tesla Model 3 (2024) review: the new electric standard
This refined version of the best-selling electric car sets a new standard for EVs

FiiO R9 review: the ultimate desktop Hi-Fi experience
An auditory Swiss Army Knife that delivers on all fronts, with a premium price tag to match

Nothing Ear (a) review: hello yellow
Colourful, cut-price take on Nothing’s usual formula goes one better in a few key areas

Nothing Ear review: definitive article
Third time lucky for Nothing’s ace affordable in-ears

Maserati Grecale Folgore review: tempting transition EV
Luxurious, powerful, and yes, very expensive
Motorola Buds+ review: with a little help from my friends
Moto brings in Bose for affordable ANC expertise

The best of everything
Stuff Picks
Atari 2600+ retro console will play your old cartridge games
You’ll want to cart home this retrogaming beauty and party like it’s 1979

Apple Watch Series 9 vs Ultra 2: what’s the difference?
The mainstream model takes on the fitness-focused flagship

Google Pixel 7a vs Pixel 7: what’s the difference?
The latest affordable Pixel might tread on its bigger brother’s territory
Dyson Zone: what you need to know about the crazy air-purifying headphones
The Dyson Zone is very real, despite looking like a device from a dystopian Sci-Fi movie












